A new variant of the Gameover Malware is targeting job seekers and recruiters by attempting to
steal log-in credentials for Monster.com and CareerBuilder.com. A
computer infected with Gameover ZeuS will inject a new 'Sign In' button into
the Monster.com sign-in page, but the
page looks identical.
Sunday, March 30, 2014
Thursday, March 20, 2014
Week two starts of with a bang.
Week
two of Information Security class and Slashdot reports Malware Attack Infected
25,000 Linux/UNIX Servers.
Security
researchers from ESET have identified an attack campaign that has infected more
than 25,000 Linux and Unix servers. The servers are being hijacked by a Trojan horse.
ESET is calling the attack “Operation Windigo”
For a long time, many people believed viruses and malware were only a Windows issue. However over the years people have come to the conclusion that Windows devices are not the only thing you need to worry about.
For a long time, many people believed viruses and malware were only a Windows issue. However over the years people have come to the conclusion that Windows devices are not the only thing you need to worry about.
In other news, Google
made Gmail exclusively HTTPS. Gmail now requires HTTPS and all email
will be sent
encrypted. They have always supported HTTPS and in 2010 they made it the default, but until this week it was not mandatory. This ensures all messages are
encrypted while they transverse their
servers and
through datacenters.
Saturday, March 15, 2014
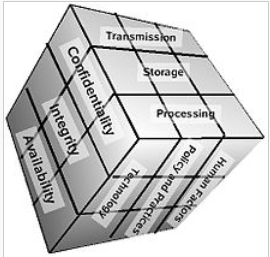
McCumber Cube
Welcome to my blog. I am new at blogging,
and
I am looking forward to developing a new skill. I hope you enjoy the blog and come back again as it develops.
This week’s discussion was about the McCumber Cube model, and how it can help with your company security. This model is portrayed in a Rubik’s Cube like design and is good at establishing information security programs.
This week’s discussion was about the McCumber Cube model, and how it can help with your company security. This model is portrayed in a Rubik’s Cube like design and is good at establishing information security programs.
Subscribe to:
Comments (Atom)